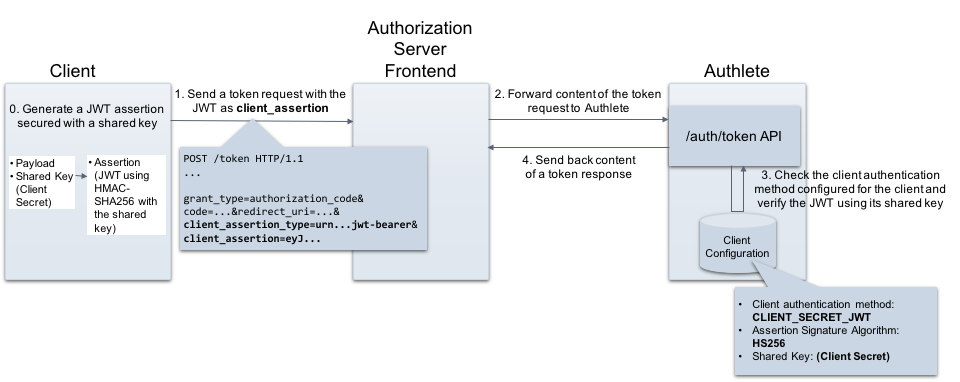
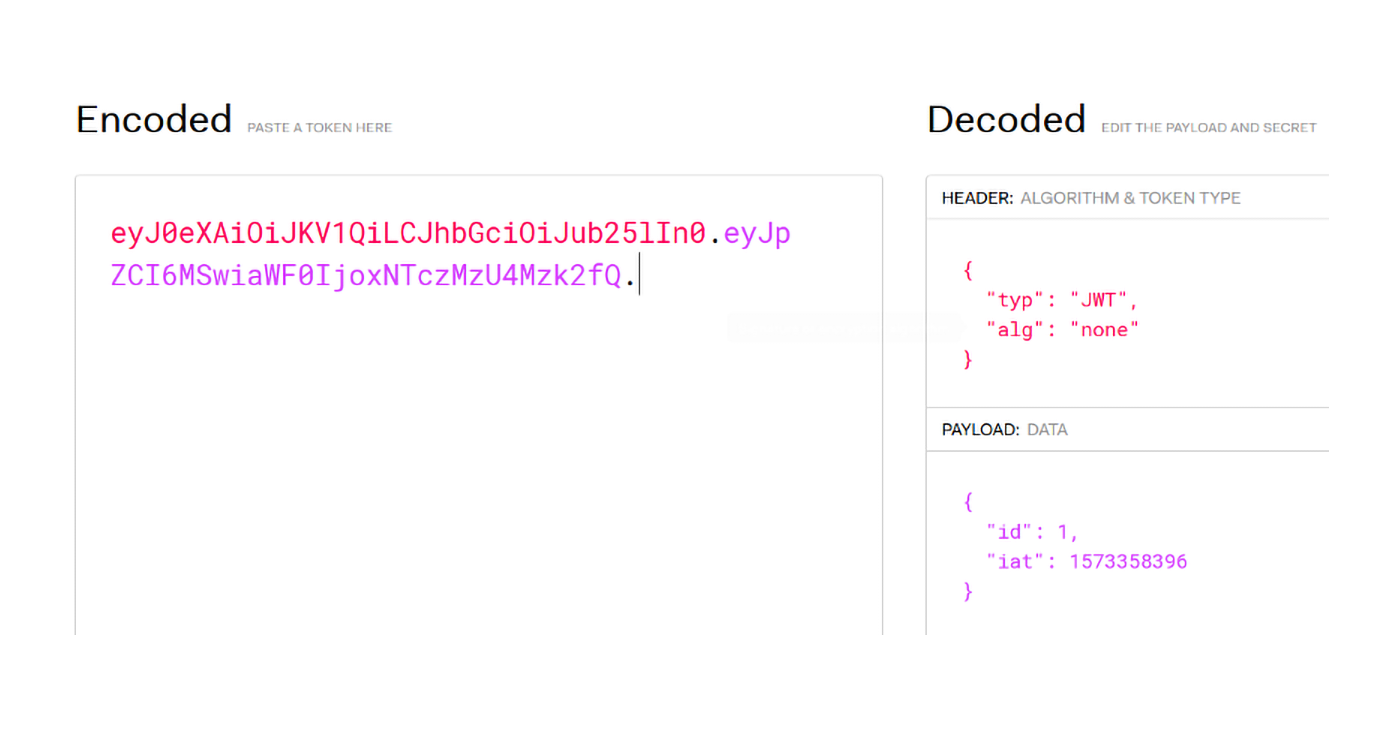
How to get Secret Key of JWT by Dictionary Attack | JWT_TOOL Github Review with RockYou.txt file - YouTube
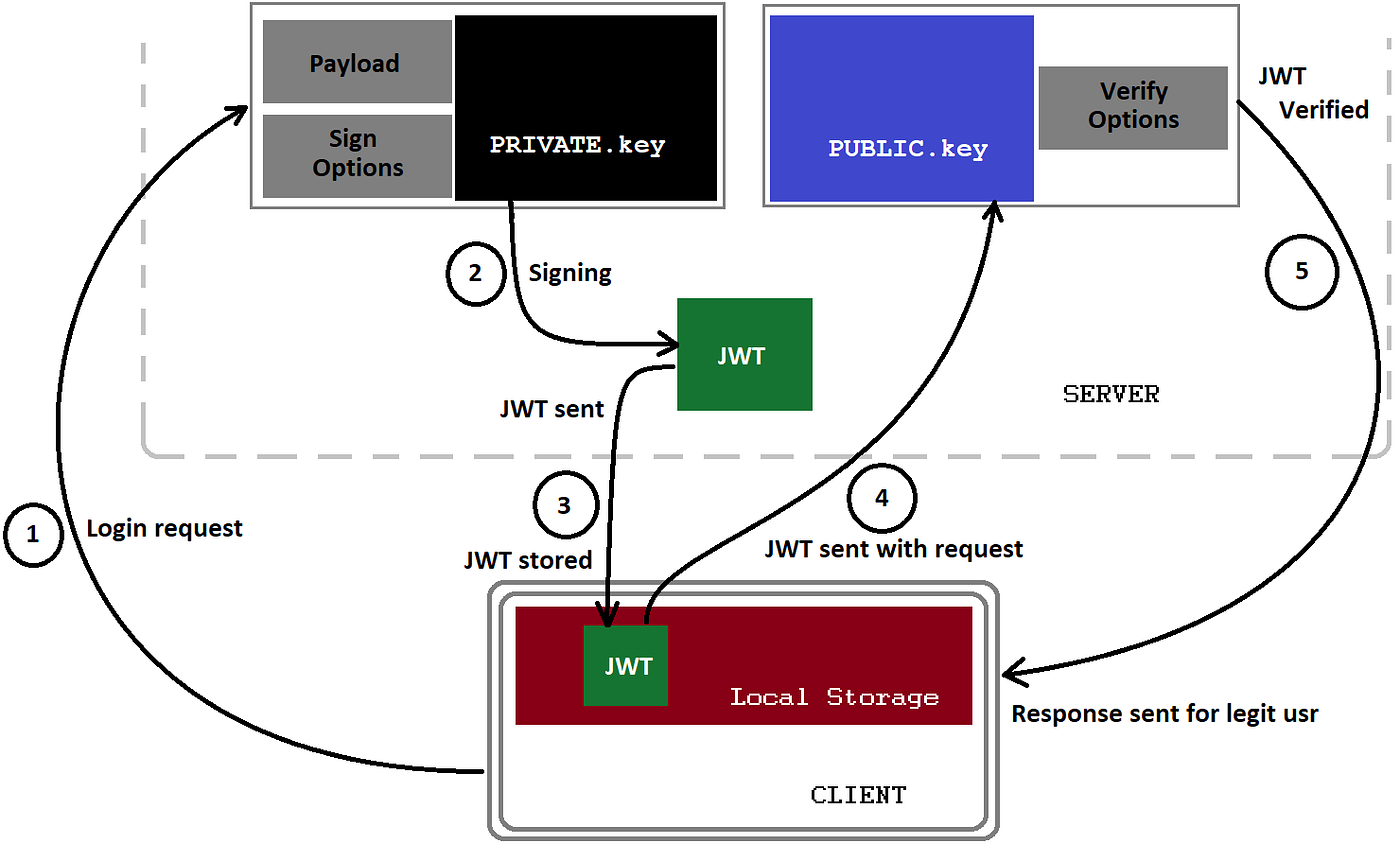
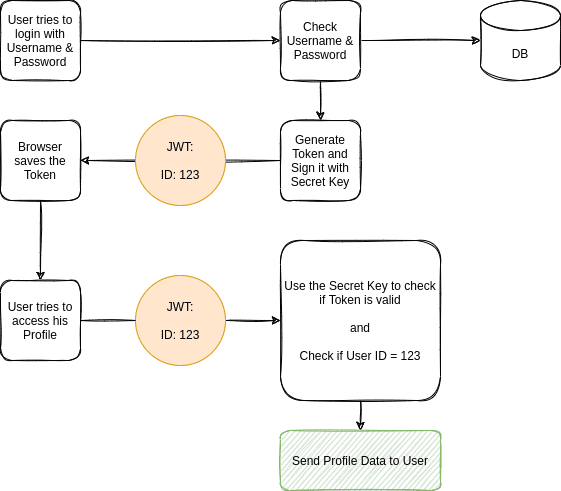
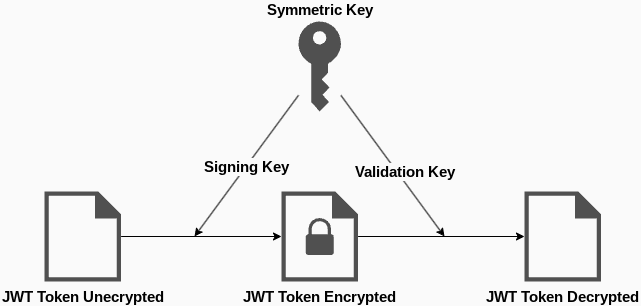
JWT Authentication using Node.js. SON Web Tokens (JWTs) are a popular way… | by Android & Node js | Medium

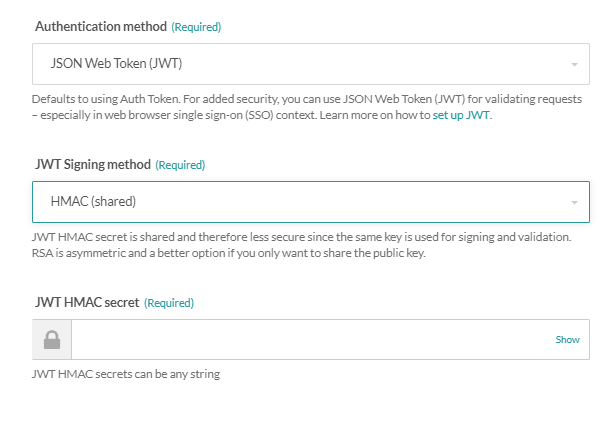
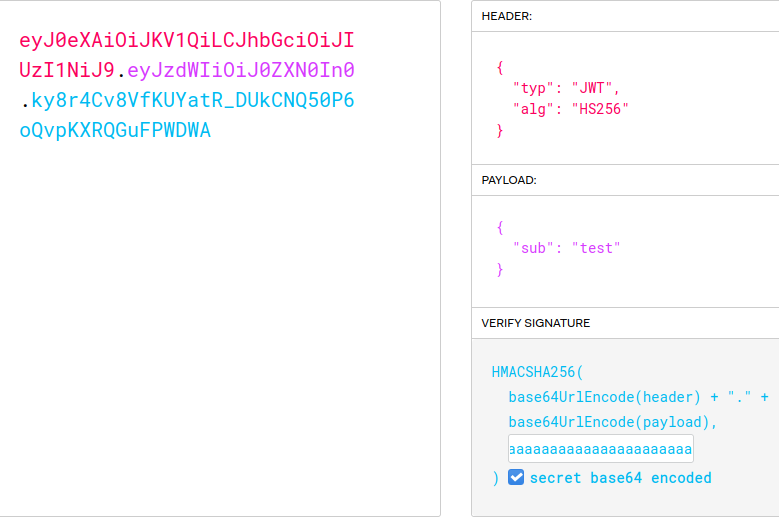
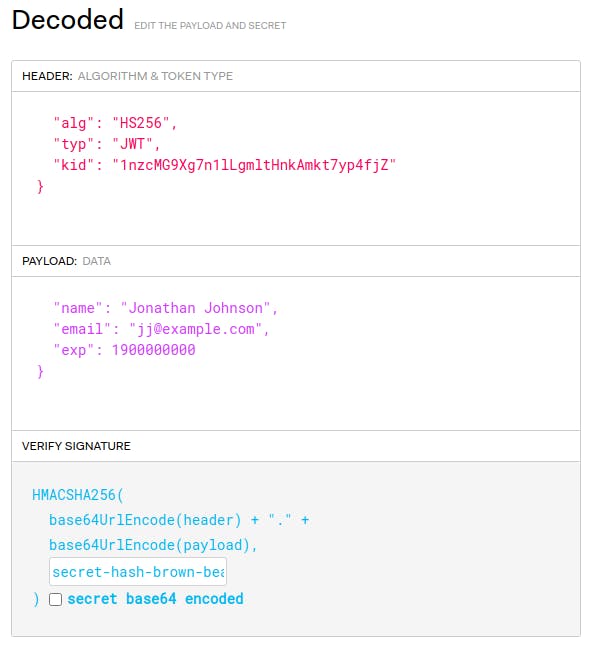
Understanding what is the process of "secret base64 encoded" when user click on the tick button - Auth0 Community